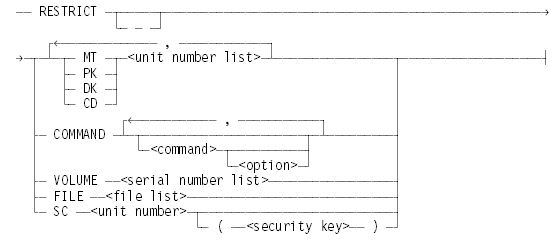
The RESTRICT (Set Restrictions) command sets or resets security-related restrictions on peripherals, volumes, commands, or files. The system preserves the restricted status of a unit and its security key through a halt/load. This command initiates an independent runner named RESTRICT <device type> <unit number>.
The COMMAND option enables the security administrator to set or reset security restrictions on system commands. Restricting the use of certain commands can help to prevent changes to the system configuration. Command restrictions are in effect only when security administrator status is authorized by the ??SECAD (Security Administrator Authorization) command.
Users or programs must have security administrator privileges if they want to use more than the inquiry forms of the RESTRICT command.
Syntax
<file list>

Explanation
RESTRICT MT <unit number list>
Marks the specified tape units as restricted. The RESTRICT − MT <unit number list> command removes the restrictions from the units.
RESTRICT PK <unit number list>
RESTRICT DK <unit number list>
Mark the specified packs or memory disk units as restricted. If the command specifies one pack in a multipack family, all packs in the family are treated as restricted even if they are not so marked.
The RESTRICT − PK <unit number list> or RESTRICT − DK <unit number list> command removes the restrictions from the packs. To remove the restrictions from a family, the RESTRICT − command must specify all members of the family that are marked as restricted.
RESTRICT CD <unit number list>
Marks the specified CD-ROM units as restricted. You can use the RESTRICT − CD <unit number list> form of the command to remove the restrictions from the specified units.
RESTRICT COMMAND
Displays a list of the restricted commands.
Note that many commands are automatically restricted when a security administrator is authorized. For a complete list of these automatically restricted commands, refer to the ??SECAD (Security Administrator Authorization) primitive command.
RESTRICT COMMAND <command>
Restricts the use of the specified command. The following commands can be specified in the RESTRICT command.
|
ACCOUNTING |
DL |
MAX |
SBP |
|
AD |
DMSDELAY |
MDT |
SECOPT |
|
AI |
DN |
ML |
SEGARRAYSTART |
|
AR |
DQ |
MOVE |
SF |
|
ARCCONVERT |
DR |
MP |
SHARE |
|
ARCCOPY |
DRC |
MQ |
SI |
|
ARCDUPLICATE |
EXPAND |
MU |
SL |
|
ARCREPLACE |
FAMILYACCESS |
NA |
SQUASH |
|
ASD |
HLUNIT |
NET |
SS |
|
BNAVERSION |
HN |
NEW SYSTEMDIRECTORY |
STRUCTURECACHE |
|
CF |
HS |
OP |
SUPPRESSWARNING |
|
CM |
HU |
PB |
SYSOPS |
|
COMPILERTARGET |
ID |
PQ |
TERM |
|
COPYCAT |
IK |
RB |
TL |
|
CPURATEBIAS |
IODELAY |
RECONFIGURE |
TR |
|
CS |
LC |
RES |
UQ |
|
DD |
LG |
RESTRICT |
XD |
|
DF |
LICENSESTATUS |
RP |
|
|
DISKKEY |
LOGGING |
SB |
-
Not all these commands are available on all MCP releases.
-
For specific restrictions associated with the IK system command, refer to the MCP Security Overview and Implementation Guide.
-
Commands that are automatically restricted when the security administrator status is enabled can be the target of a RESTRICT COMMAND command, but the inclusion of these commands has no effect.
-
CPURATEBIAS, DMSDELAY, and IODELAY commands are only restricted through the ODT interface. They can still be used through the SETSTATUS interface.
-
Unlike other commands, if the NA or NET command is restricted, then all forms of the command—whether interrogatory or not—are restricted. The exception is the simple NET command, which elicits a response indicating status for all networks.
If security administrator status is authorized for the system, restricted commands can be entered only from a source with SECADMIN status. Such sources include
-
A MARC session with a security administrator usercode.
-
A program using SETSTATUS that is running under a usercode with SECADMIN status.
-
A program using DCKEYIN that is marked with SECADMIN status by the MP (Mark Program) command.
| Note: | Setting the TERM USER attribute to a security administrator usercode at an ODT does not permit the use of restricted system commands from that ODT. |
RESTRICT COMMAND <command> <option>
Restricts the use of the specified command option. Option can be any valid reserved word. You can use options to restrict a variation of the command rather than to restrict all uses of the command. For example, if you restrict SYSOPS, you restrict all uses of the command. If you restrict SYSOPS LANGUAGE, you restrict only the LANGUAGE option of the SYSOPS command.
| Note: | Because <option> can be any valid reserved word, an invalid combination of words is not rejected. For example, DL CM is accepted but does not cause any command to be restricted. |
RESTRICT − COMMAND <command>
Removes any restrictions previously applied on the specified command.
RESTRICT VOLUME <serial number list>
Marks the volume directory entries for the specified tape volumes as restricted. RESTRICT − VOLUME <serial number list> removes the restrictions from the tape volumes. This command is available only if you are using Secure Access Control Module security enhancement software and if you have set the TAPECHECK security option.
RESTRICT FILE <file list>
Marks the specified nondata files as restricted. Nondata files are system files, compilers, backup files, and code files. For a definition of these files, refer to the discussion of FILEKIND in the I/O Subsystem Programming Guide. An attempt to restrict a data file causes an error message to be displayed. The RESTRICT − FILE <file list> command removes the restrictions from the files.
RESTRICT SC <unit number>
Suspends automatic display mode (ADM) on the specified ODTs and restricts those ODTs to using MARC and being assigned to files. The execution of this command leaves the specified ODTs under the control of COMS/ODT/DRIVER. If a unit has been reserved with a UR (Unit Reserved) command, it cannot be restricted, and the following message appears:
SC <unit number> NOT RESTRICTED
If a unit is already restricted, the following response appears:
SC <unit number> RESTRICTED AGAIN
The maximum number of ODTs that can be restricted is 15. An attempt to restrict more than 15 ODTs produces the following error message:
SC <unit number> NOT RESTRICTED, TOO MANY RESTRICTED ODTS
You can use the following system commands on a restricted ODT:
-
In ODT mode, the following commands are valid:
-
??MARC
-
??RESTRICT (<security key>)
-
LABEL
-
-
In MARC mode, you can use only ??ODT.
RESTRICT SC <unit number list> (<security key>)
Restricts the specified ODTs to using only MARC and being assigned to files, and associates a security key with them.
The security key specification is invalid with the RESTRICT − SC <unit number list> form of the command. The security key option enables you to remove the restriction from the ODT later with the primitive command ??RESTRICT as long as you know the security key. If you do not specify security key information in the RESTRICT command, you must have privileged system access (or access to an unrestricted ODT) to remove the restriction.
RESTRICT − SC <unit number list>
Removes the restriction on the use of the specified ODTs, whether or not they have a security key. The system places the ODT in ODT mode (rather than MARC mode). When the system releases an ODT, automatic display mode (ADM) becomes enabled.
If an ODT is not restricted, the following message appears:
SC <unit number> RELEASED AGAIN
If an ODT is reserved (with a UR command), it cannot be released and the message is
SC <unit number> NOT RELEASED
Examples
Example 1
The following are examples of how security-related restrictions on peripherals, tape volumes, or files can be set or reset through the RESTRICT command.
|
Command |
Action |
|---|---|
|
RESTRICT MT 113-115 |
Marks tape units 113 through 115 as restricted. |
|
RESTRICT PK 201 |
Marks pack 201 as restricted. |
|
RESTRICT − PK 201-203 |
Marks packs 201 through 203 as unrestricted. |
|
RESTRICT − MT 113, PK 208-211 |
Marks tape unit 113 and packs 208 through 211 as unrestricted. |
|
RESTRICT VOLUME 123456 |
Marks the volume directory entry for the tape volume with the serial number 123456 as restricted. |
|
RESTRICT FILE X |
Marks the file named X on DISK as restricted if it is a non-data file. |
|
RESTRICT − FILE X ON PACK |
Marks the file X ON PACK as unrestricted. |
Example 2
The following examples show how security-related restrictions on an ODT can be set or reset through the RESTRICT SC <unit number list> command.
|
Command |
Action |
|---|---|
|
RESTRICT SC 1 |
Restricts the ODT whose unit number is 1. |
|
RESTRICT − SC 1 |
Removes the restriction on the ODT whose unit number is 1. |
Example 3
The following examples show how security-related restrictions on a command can be set or reset through the RESTRICT COMMAND <command> <option> command.
|
Command |
Action |
|---|---|
|
RESTRICT COMMAND SYSOPS LANGUAGE |
Restricts the use of the LANGUAGE option of the SYSOPS command. |
|
RESTRICT − COMMAND SYSOPS |
Removes any restrictions on the SYSOPS command. |
|
RESTRICT COMMAND MAX |
Restricts the use of all options of the MAX command. |
|
RESTRICT − COMMAND MAX MESSAGES |
Removes the restriction on the MAX MESSAGES command. |
Example 4
Suppose a family consists of two packs numbered 61 and 62, both unrestricted. The command RESTRICT PK 61 causes pack 61 to be marked as restricted and pack 62 to be treated as restricted even though it is not so marked. The command RESTRICT − PK 61, which removes the restriction on pack 61, also stops the restricted treatment of pack 62. By contrast, if both packs had been marked as restricted, the command RESTRICT − PK 61-62 would have been needed to remove the restrictions from the family.
Considerations for Use
If security administrator status is authorized on the system the RESTRICT command can be issued only by a security administrator usercode. If security administrator status is not authorized on the system, then any operator, SYSTEMUSER, or privileged user can issue RESTRICT commands. For information about setting security administrator status, refer to the ??SECAD (Security Administrator Authorization) primitive command.
Restricting Commands
The RESTRICT COMMAND enables the site to specify that some system commands can be used only by a Security Administrator.
Only the Security Administrator can use the RESTRICT COMMAND system command. When security administrator status is enabled on the system, some commands, for example the SL (Support Library) command, are automatically restricted.
Restricting Files, Units, and Volumes
Access restrictions might affect file copying by library maintenance. The access restriction for the new file is unpredictable if the file, volume, or unit restrictions of either the source or destination are changed while copying is in progress. These restrictions should not be changed during copying of any file that might be affected.
Access to a nondata file is restricted if one or more of the following conditions is true:
-
The file is explicitly restricted.
-
The volume containing the file is restricted.
-
The unit on which the volume is mounted is restricted.
-
The file is on a pack or memory disk family with one or more members located on a restricted unit.
Code files to which access is restricted cannot be executed. Such files can be opened only by a security administrator (or, if security administrator status is not authorized, by a privileged user). These files can be altered if they can be opened and if system criteria for altering them are met.
A nondata file to which access is restricted can be copied on the local system by a security administrator or, if security administrator status is not authorized, by a privileged user.
If access to a unit is restricted, access to any volume mounted on the unit is also restricted. If a volume is restricted, access to all files on that volume is also restricted. Access to a file is unrestricted only if access to the unit and volume where it resides, as well as to the file itself, is unrestricted. Removing the restriction from a file on a restricted unit without also removing the restriction from the unit results in a warning that access to the file remains restricted.
When library maintenance copies a file from one volume to another, the access restriction imposed on the copy depends on the access restrictions at the source and at the destination. Copying a restricted file to any unit produces a restricted file. Copying an unrestricted file from a restricted unit to an unrestricted one produces a restricted copy. Copying an unrestricted file from an unrestricted volume on an unrestricted unit produces an unrestricted file, unless the destination volume or unit is restricted, in which case the copy is restricted.
Restricting an ODT
The command to restrict an ODT can be entered at that ODT, at any other ODT, at any terminal that has privileged system access through MARC, or by a privileged user.
You can restrict an ODT is scratch, labeled, or saved. You can restrict an ODT that is the target of the PS (Print System) ASSOCIATE or UQ (Unit Queue) command. You cannot restrict an ODT if it is reserved, freed, or assigned to a file. However, you can reserve a restricted ODT with a UR (Unit Reserved) command or a FREE (Free Resource) command if the ODT is not in use; its restricted status is preserved.
You can remove the restriction from an ODT by entering ??RESTRICT − <key> or, if you have privileged system access, from a MARC session by entering RESTRICT − SC <unit number list>.
If all ODTs become restricted, you must perform a cold-start.