Use the SYSADMIN COMMAND system command to control operator access to system commands that are considered to be sensitive and that can change the system state. Such commands are considered to be sensitive and are restricted to use by a system administrator.
A system administrator is a user with the usercode attribute SYSADMIN set.
Commands related to the mix are not restricted
You must have special privileges to use certain forms of this command. Refer to “Considerations for Use” for more details.
Syntax
Explanation
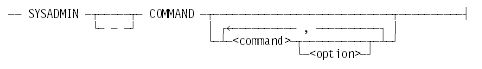
SYSADMIN COMMAND
Displays a list of the commands restricted to system administrator use. Use of this form of the command does not require special privileges. You can enter this form of the command from any source.
SYSADMIN COMMAND <command>
Restricts the use of the specified command to a system administrator. You can restrict the use of the following system commands.
|
ACCOUNTING |
DMSDELAY |
MDT |
SECOPT |
|
AD |
DN |
ML |
SEGARRAYSTART |
|
AI |
DQ |
MOVE |
SF |
|
AR |
DR |
MP |
SHARE |
|
ARCCONVERT |
DRC |
MQ |
SI |
|
ARCCOPY |
EXPAND |
MU |
SL |
|
ARCDUPLICATE |
FAMILYACCESS |
NA |
SQUASH |
|
ARCREPLACE |
HLUNIT |
NET |
SS |
|
ASD |
HN |
NEW SYSTEMDIRECTORY |
STRUCTURECACHE |
|
BNAVERSION |
HS |
OP |
SUPPRESSWARNING |
|
CF |
HU |
PB |
SYSOPS |
|
CM |
ID |
PQ |
TERM |
|
COMPILERTARGET |
IK |
RB |
TL |
|
COPYCAT |
IODELAY |
RECONFIGURE |
TR |
|
CPURATEBIAS |
LC |
RES |
UQ |
|
CS |
LG |
RESTRICT |
XD |
|
DD |
LICENSESTATUS |
RP |
|
|
DF |
LOGGING |
SB |
|
|
DL |
MAX |
SBP |
| Note: | Not all these commands are available on all MCP releases. |
The CPURATEBIAS, DMSDELAY, and IODELAY commands are only restricted through the ODT interface. They can still be used through the SETSTATUS interface.
Note that, unlike other commands, if NA or NET are restricted, then all forms of the commands, whether interrogatory or not, are restricted, with the exception of the simple NET command which elicits a response indicating status for all networks
The following commands are automatically restricted when security administrator status is enabled. If security administrator status is enabled, a system administrator cannot use them even if they are added to the list of SYSADMIN COMMAND commands.
-
ACCOUNTING
-
CF
-
DL with the following options:
-
LOG
-
USERDATA
-
-
HU
-
ID with the following options:
-
−
-
<file name>
-
-
LG
-
LOGGING
-
MP with the following options:
-
COMPILER
-
EXECUTABLE
-
IDENTITY
-
KERBEROS
-
PU
-
SECADMIN
-
SERVICE
-
TASKING
-
All granulated privileges
-
-
MU
-
REMOTESPO :OK
-
RESTRICT
-
SECOPT
-
SL
-
SYSADMIN
SYSADMIN COMMAND <command> <option>
Restricts the use of the specified command option to a system administrator. The value of <option> can be any valid reserved word. You can use options to restrict a variation of the command rather than to restrict all uses of the command. For example, you might want to restrict only usage of the LANGUAGE option of the SYSOPS command.
| Note: | Because <option> can be any valid reserved word, an invalid combination of words is not rejected. For example, DL CM is accepted but does not cause any command to be restricted. |
SYSADMIN − COMMAND <command>
Removes any restrictions previously applied to the specified command.
Examples
Example 1
This example restricts the use of the MERGE option of the IK system command.
SYSADMIN COMMAND IK MERGE
Example 2
This example removes the usage restriction on the IK system command.
SYSADMIN - COMMAND IK
Example 3
This example sets usage restrictions on the TL system command and the LANGUAGE option of the SYSOPS system command.
SYSADMIN COMMAND TL, SYSOPS LANGUAGE
Example 4
After a security administrator issues the following two commands, both security administrators and system administrators can use the SYSOPS system command.
RESTRICT COMMAND SYSOPS
SYSADMIN COMMAND SYSOPS
Example 5
After a security administrator issues the following command, the system administrator can issue a SQUASH system command, but the security administrator cannot.
SYSADMIN COMMAND SQUASH
Example 6
After a security administrator issues the following command sequence, only the security administrator can issue a SQUASH system command.
SYSADMIN COMMAND - SQUASH
RESTRICT COMMAND SQUASH
Example 7
After a security administrator issues the following request, only the security administrator can issue a TL system command.
RESTRICT COMMAND TL
Considerations for Use
Levels of Security Required to Use This Command
A system administrator is a user with the SYSADMIN usercode attribute.
If security administrator status is authorized on the system, restrictions on system commands can be set only by someone who has a security administrator usercode.
If security administrator status is not authorized on the system, restrictions on system commands can be set only by a system administrator. For information about setting security administrator status, refer to the ??SECAD (Security Administrator Authorization) primitive command.
Sources for Entering Restricted Commands
You can enter restricted commands only from a source that has SYSADMIN user status. Such sources include
-
A MARC session with a system administrator usercode
-
A program using SETSTATUS that is running under a system administrator usercode
-
A program using DCKEYIN that is running under a system administrator usercode
| Note: | Setting the TERM USER attribute to a security administrator usercode at an ODT does not permit the use of restricted system commands from that ODT. |
Precedence for Using SYSADMIN COMMAND and RESTRICT COMMAND Commands
When security administrator status is authorized, the following rules apply:
-
Only a security administrator is permitted to use the SYSADMIN COMMAND to add or delete restricted commands. This usage permits the security administrator to determine which commands the system administrator usercode can control. The system administrator cannot change the set of commands that has been delegated by the security administrator.
-
The security administrator can give the system administrator exclusive rights to a particular command and options, or he can retain the rights to that particular command and option for himself.
-
If a security administrator delegates the control of a command to a system administrator, the security administrator is not permitted to use that command until it has been removed from the control of the system administrator with the SYSADMIN - COMMAND system command.
-
A security administrator can permit a command to be used by both a system administrator and a security administrator. You can accomplish this by naming the command using both the RESTRICT COMMAND and SYSADMIN COMMAND, shown in Example 4.
-
A user who has both security administrator and system administrator privileges is not subject to command restrictions.
Examples 4 through 7 illustrate the precedence for use when security administrator status is authorized.